Cybersecurity: Control Systems Are Under Attack
William L. Mostia, PE, Fellow SIS-TECH Solutions is a frequent contributor to Control.
In 2010, the control industry was turned on its head when control systems manufactured by Siemens suffered an attack by the Stuxnet cyber worm. It appears that while the worm was turned into the wild, it was harmless unless it discovered its intended target—the control system that controlled the uranium processing equipment in Iran. There is speculation that the worm was developed by Israel and the United States to attack Iran's nuclear bomb program and may be one of the first "weaponized" cyber attacks. This brought cybersecurity for control systems into the sunlight.
Subsequent Stuxnet derivatives Duqu and Flame do not appear to be weaponized, but appear to be data collection malware. Experts speculate that they were designed to collect data to give intruders the ability to easily conduct a future attack against potential third-party targets. All this may well represent a call to arms in the developing cyber war in our little piece of the universe. However, there may be a potential upside to Stuxnet, for as a wise man, Edgar Watson Howe (1853-1937), observed, "A good scare is worth more to a man than good advice."
This article concerns itself with the narrow domain of process control, which we consider to include the basic process control systems (BPCS), i.e. DCS, PLC, field instrumentation and safety systems in the process industries. The process control cyber domain will normally also include supervisory control and data acquisition (SCADA) systems.
Also Read: Cyber vulnerabilities in control systems
Critical Infrastructure Sectors
The U.S. Presidential Policy Directive 21 (PPD-21), "Critical Infrastructure Security and Resilience," identifies critical infrastructure sectors, which include the chemical and energy sectors. The Department of Homeland Security (DHS) formed the Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) to work with law enforcement agencies and the intelligence community, and to collaborate with international and private sector computer emergency response teams (CERTs) to share control systems-related security incidents and mitigation countermeasures.
ICS-CERT also provides a Cybersecurity Evaluation Tool (CSET), a desktop software tool that guides users through a step-by-step process to assess their control system and information technology network security practices against recognized industry standards. CSET provides a prioritized list of recommendations for improving the cybersecurity posture of the organization's enterprise and industrial control systems. This discussion is primarily applicable to process control, but many of the aspects discussed here apply to the broader area of industrial automation.
Process Control Systems vs. IT Systems
Process control systems and IT systems both use computer systems to achieve their goals. The IT systems are typically used in chemical, refining or oil and gas production companies for a wide range of purposes, including employee workstations, engineering, human resources and accounting. These companies produce chemical and refining products, often using inherently dangerous processes that are kept under control through process control and safety systems. These system use a mixture of commercial off-the-shelf (COTS) technology systems, e.g., Windows-based computer systems, Ethernet, etc.; purpose-manufactured computer systems such as DCSs, PLCs, smart field instruments; and bespoke control and monitoring systems. This creates a diverse cyber environment where the hardware and software configuration will be unique to each process controlled, and the cyber risk profile will vary on an installation-to-installation basis. There will also be commonalities, such as industry-common communication architectures, and similarities associated with a particular brand of DCS or PLC.
Process control and IT also have different priorities and vested interests. The general information technology computing system domain priorities are protection of data (confidentiality, loss prevention, data integrity, etc.), continuation of service and system integrity.
The priorities of the process control domain are safe operation, availability (high uptime, high production rates), quality (on-spec product), and efficiency (lowest production cost).
Theft of control data, while a consideration, is not a top concern unless it would directly impact one of the above four priorities. The exception to this might be loss of proprietary recipes. Damage to control databases or damage to required regulatory databases would impact the four control priorities.
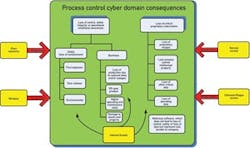
The consequences of a breach are substantially different for IT and process control systems. Breaching an IT system can have substantial financial, loss of privacy and denial of service consequences. Successfully breaching a process control system could lead to threats to life and limb (loss of containment leading to fire, explosion or release of toxic material), damage to the environment and significant financial loss. Figure 1 illustrates some, but not all, of the potential consequences in the process control systems.
Failure to understand the difference between the process control systems and the facility IT networks can lead to unnecessary conflict between the process control department and the IT department. Process control cybersecurity requires close collaboration between the process control department and the IT department because many of the threats to a process control system may come through the facility's computer network or enterprise IT systems, and many of the vulnerabilities come from COTS devices used in the process control system. A quote by Benjamin Franklin comes to mind here: "We must all hang together, or assuredly we shall all hang separately."
Vulnerability of Process Control Systems
Figure 1: A break-in of your systems through a cyber attack can have many far-reaching and expensive consequences.
Industrial automation and control systems have become more vulnerable to potential cyber threats over time due to the following trends:- Increased use of COTS technology and protocols in control systems;
- The demand for open systems;
- Enterprise and plant computer system integration;
- The trend to outsource engineering and technical support to third parties, as well as the design and manufacturing of control hardware and software;
- Increased use of joint ventures that creates more potential access vulnerabilities;
- Demand for remote access both internal and external to the company;
- Increased availability of online documentation for control systems.
All is not lost, though. Legacy systems can sometimes provide some protection against cyber attack. Some of these protections include:
- Proprietary design of hardware and digital networks (particularly prior to the Windows invasion of HMIs);
- Diverse hardware with limited integration, e.g., different hardware for DCS, PLC, safety systems, etc.;
- Lack of situational knowledge of the process under control;
- Control of writes in PLC and safety systems (a control system philosophy that goes back to the early 1980s);
- Specific expertise in control systems, including legacy hardware, architecture, interconnection and configuration;
- A physical "write protect" jumper in many field devices and keylock program protect in PLCs (assuming the manufacturer has not left in a backdoor, remote, software override);
- The risk-based layer of protection philosophy and SIS standards in place in the past 20 years, which provides protection against loss of containment, but not necessarily against financial losses due to a loss of control.
Also Read: Who Is to Blame for Our Control Systems' Vulnerability?
There is clear and convincing evidence of the threat of cyber attacks on business and personal computers, and there is a clear belief that control systems are potentially vulnerable to cyber attack, but there was also a general lack of public specifics (even scrubbed ones) of the actual successful external cyber attacks to process control systems that led to a loss of control and the result thereof.
Stuxnet and its derivatives are the most bandied about bogeyman, but many times by people who are obviously not knowledgeable in process control. This may be due in part to the normal corporation defensive mechanism of circling the wagons when it comes to releasing information that might be perceived as a weakness, give an advantage to an competitor, or create perceived legal liabilities. There may be some relief in sight with the new Oil and Natural Gas Information Sharing and Analysis Center (ONG-ISAC), which will facilitate the exchange of information to help evaluate risks and provide up-to-date security guidance to U.S. companies. While the American Petroleum Institute (API) helped form this ISAC (one of 17 sector-based ISACs), it will be a standalone organization, headquartered in Washington, D.C., and supported by industry.
This lack of specifics unfortunately puts control engineers in the unenviable position of being told that the barbarians are surely at the gate, but not knowing who, what and, most important, how they will get through the gate, and what they will do if they do.
Cybersecurity is often a reactionary business, reacting to the next virus or cyber worm du jour, and that will always be the case as long as there are new zero-day vulnerabilities to be found. It is also possible to be proactive by understanding the cyber attack within the context of the control and safety system environment, and limiting the potential negative effects through the uses of countermeasures and the native control and safety system design.
New System Considerations
Purchasing a new control system today should get you control systems that conform to international standards such as ISA99/IEC 62443: "Industrial Network and System Security" or the WIB–Process Automation Users Association's standard, "Process Control Domain Security Requirements for Vendors." (If the one you have in mind doesn't conform, buy a different system). There are also organizations and companies that certify equipment and engineering processes to these standards such as the ISA Security Compliance Institute's ISASecure (IEC 62443) or Wurldtech's Achilles Practices Certification.
Several things need to be noted about installing new systems. The first is that new systems will be installed into a constantly evolving cybersecurity environment where a new system can become a vulnerable legacy system overnight if care is not taken, which makes lifecycle and sustainability considerations important. The second is that with the potential exception of an isolated greenfield plant, the new system will be installed into an existing cybersecurity infrastructure with its weaknesses and strengths. Third, certified hardware/software, while helpful, alone does not guarantee adequate protection against cyber attacks. To address these issues, a cybersecurity risk assessment should be performed in the FEED stage of the project and on the final installed design. This assessment should include cybersecurity from a system lifecycle perspective because, like safety, it's an ongoing war and not just a battle or skirmish, to maintain the integrity of the system over its lifetime.
Manufacturers of the control equipment also typically provide purpose-built control system firewalls for new and existing systems, as do many OEMs. Many of these are based on Belden/Tofino Security's deep packet inspection technology. Examples of this are Honeywell's Experion Process Knowledge System (PKS) series, consisting of three pre-configured Tofino security appliances—Modbus TCP Firewall, OneWireless Firewall and Modbus Read-Only Firewall; Schneider Electric/Invensys/Triconex's Tofino Firewall; and Crouse-Hinds/MTL's Tofino Industrial Security System. Other examples of control system industrial security appliances are the Waterfall for Modbus and the Unidirectional Security Gateway from Waterfall Security and Deep-Secure's Modbus Guard appliance.
In addition, more discussions of firewalls in process control application can be found in the following two references, including "Firewall Deployment for SCADA and Process Control Networks Good Practice Guide" from the Center for the Protection of the National Infrastructure, 2005 and "Next Generation Firewalls for Industrial Control and Automation Systems (ICAS) Security."
Existing Systems
Existing control systems represent a wide spectrum of technologies and designs spread over 40 years of the control system digital era. Some of the vulnerabilities and hidden strengths of existing systems were discussed above. The biggest vulnerability is probably the use of COTS Microsoft products in control systems coupled with Ethernet interconnectivity and removable storage media (e.g., thumb or stick drives).
Everyone the author interviewed for this article agreed that the first step for an existing system was a cybersecurity risk assessment. Eric Byres, chief technology officer at Tofino Security, suggests as a second step that the user should identify the "family jewels" and protect them. High-risk processes' vulnerabilities should also have priority. Any low-hanging fruit should be next, and then plan to remediate the rest of the vulnerabilities in a timely manner based on the risk level. As with safety, the risk you do not mitigate is risk you assume.
The Cybersecurity Evaluation Tool self-evaluation tool was discussed above. There are third-party vendors who provide these risks assessments and other cybersecurity services; e.g., aeSolutions, exida, Kenexis and others. The major control system manufacturers also provide cybersecurity services. Before one starts this journey, the control and safety systems' manufacturer(s) should be contacted to see what help they can provide.
What to Do Once You Know
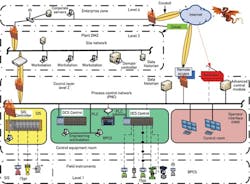
Once your risk assessment is complete, a risk mitigation plan should be developed to address the cybersecurity risk assessment recommendations in a timely manner based on the identified level of risk and operational timing. The common protection approach is a layered approach, that is, "defense in depth" similar in concept to safety's layer of protection methodology. In this approach, the computer architecture is divided into conduits (access paths) and zones (grouping of instrumentation and controls with a common functionalities). Figure 2 is based on the four-zone approach in ANSI/ISA–99.02.01–2009. Firewalls or security appliances are typically used to control the conduits (access paths) to protect from cyber threats passing from one zone to another. Software-based protection on individual computers is typically provided for at the system level, and more secure control hardware may be installed in the high-risk zones.
Figure 2: In this approach, firewalls or security appliances are used to control the conduits (access paths) to protect from cyber threats passing from one zone to another.
Cybersecurity is to a large extent a matter of controlling the external and internal unauthorized access to the process control system and the control of unauthorized or inadvertent changes. Access controls such as passwords, keylocks, pass cards, etc. should be maintained, and all unused logical and hardware ports should be turned off or, in the case of USB ports, locked out.
Standards
The ISA99/IEC IEC 62443 group of standards is a good place to start your journey into the world of cybersecurity. ANSI/ISA-99.00.01-2007 (currently under revision as ISA/IEC 62443-1), "Security for Industrial Automation and Control Systems Part 1: Terminology, Concepts, and Models" provide a good beginning.
ISA S84 committee has also developed a technical report ISA-TR84.00.09-2013, "Security Countermeasures Related to Safety Instrumented Systems (SIS)," to provide cybersecurity guidance for SIS. In addition, the new update to IEC 61511 will require that a security risk assessment be carried out to identify the security vulnerabilities of the SIS.
AIChemE CCPS has also published Cybersecurity for Executives: A Practical Guide.
Detection and Recovery
We've been talking the threats and countermeasures, but what happens if the countermeasures don't work? The ability to detect a cyber attack and take action in a timely manner is key to limiting the potential compromised systems and the effect on the control systems. Would your operators be able to detect a cyber attack on the control system? Operators are the first line of defense for detecting abnormal behavior of the process under control. Will your automated intrusion detection systems detect the attack before it's too late? If a cyber attack were detected, how would you isolate the threat before it does too much damage, or eliminate the threat?
If there were a successful cyber attack, how would you recover? If your control databases were corrupted, how would you recover? This is an obviously a good place for a recovery plan.
Safety Systems
Safety systems in the process industries represent a layer of protection to the cybersecurity threat. This protection can include alarm, override and interlock systems in the BPCS, but the primary protection resides with the SIS and the non-instrumented IPLs such as relief valves.
Separation and independence between the BPCS and SIS has been is a key safety system philosophy. There has been a technology trend toward integration of the DCS with the SIS where the independence and separation line has become increasingly blurred from the old days when the control system and the safety system were physically separate. This trend increases the potential cyber risk exposure by reducing the separation "distance" and independence of the two systems. Countermeasures provided by the manufacturers and, in some cases, the user should ensure that any additional cyber risk due to the integration is mitigated to an acceptable level.
A properly designed safety system is not the answer to cyber threats, but it can move much of the risk back to financial ones, such as outages, reduced rates, off-spec product, increased production and maintenance costs, etc.
Conclusions
There is no doubt that cyber attacks pose a potential threat to process control systems and their associated safety systems. The process control system's cyber domain, however, has significant differences, such as priorities, computer hardware, different network architectures and mixture of different communication protocols, from the traditional IT environment. A significant difference is that a successful cyber attack on a control system that results in a loss of control can have serious life and limb consequences, as well significant financial loss should a safety incident result.
The solution is to recognize that there is a potential threat and to perform a cyber risk assessment to identify existing vulnerabilities, risks and security gaps, and to develop and implement a plan to address the cyber risks and lower them to an acceptable risk tolerance in a timely manner. The priority should be to protect the "family jewels" and high-risk processes. Cybersecurity standards are available from ISA/IEC, as is guidance from the U.S. government. It seems that for cybersecurity, there are dragons out there, but with sufficient preparedness, we can begin to defend ourselves from known threats and developing ones.
[javascriptSnippet]
William L. Mostia would like to thank the following people and their companies who took the time and patience to speak to him while this article was written:
- Eric Byres, P.E., Chief Technology Officer, Tufino Security, Belden Co;
- Mike Badi, Chief Cybersecurity Architect, Honeywell Process Solutions;
- John Cusimano, CFSE, CISSP, GICSP, Director of Industrial Cybersecurity AeSolutions;
- Eric Cosman, Co-Chair, ISA99 Committee;
- Eric Knapp, Director of Cybersecurity Solutions and Technology, Honeywell Process Solutions;
- Ian Verhappen, Principal Automation Engineer, Orbis Engineering Field Services
About the Author
William L. Mostia
William L. Mostia

Leaders relevant to this article: