Everyone knows by now that cybersecurity is a rapidly moving and evolving target. However, continually updated intelligence makes it easier to discern, aim for and hit cybersecurity goals, and gain the best odds for protecting applications and facilities. It all starts with asking a few good questions.
Based on the increasing risk and changing landscape for industrial control systems (ICS) related to cybersecurity, Air Products and Chemicals Inc., Allentown, Pa., needed to protect its worldwide footprint of more than 600 plants and facilities. Its plant managers tried to figure out what questions to answer to address industrial cybersecurity successfully. They asked: "Is my plant's ICS secure from cyber attack? Has the system been compromised already? And if I make a change to my system, will it be less secure?"
Early on, industrial cybersecurity advice typically suggests adding managed Ethernet switches used as firewalls, but follow-up questions quickly arise: What type and how many for a particular process? Do we need deep packet inspection (DPI) or an intrusion detection system (IDS)? What rules do we need configured into them? In fact, many firewalls are initially configured to permit any kind of access, so simply having one isn't good enough.
"This is why having a process hazard analysis (PHA) for cybersecurity, or cyberPHA, can add a lot of value because it can help answer questions like: How do I know when I've spent enough? How good is good enough? And, how can I avoid spending more than I have to secure my plant?" says Chris Da Costa, global plant cybersecurity manager at Air Products. He delivered a presentation with John Cusimano, industrial cybersecurity director at aeSolutions, a CSIA-member system integrator in Greenville, S.C., at the S4 ICS Security Conference in January 2017 in Miami.
Safety smartens security
One of the most approachable methods of growing industrial cybersecurity awareness and know-how in the process industries is by broadening process safety methods to embrace security, too.
Because opening spear phishing emails is one of the most common methods for downloading malware, Dan Schaffer, business development manager for networking and security at Phoenix Contact, recommends using the PhishMe software tool from CoFense, which sends sample phishing messages to a subscribing organization's staffers, reports open rates, and teaches them to avoid opening similar emails in the future.
This process enables users to determine if existing safeguards are appropriate, which will also indicate residual risk, and begin to make a comprehensive plan to address cybersecurity. These plans can consist of existing and new countermeasures, but go beyond technology to include modifying work processes, policies and procedures, and prioritizing the PHA's recommendations to determine where to spend resources where it will make the most difference.
Cusimano adds that, "Hazard and operability (HazOp) and layers of protection analysis (LOPA) studies that are typically performed for process safety generally assume that the control and safety systems will operate as designed and expected, but a PHA for cybersecurity considers deliberate actions and malicious threats to these systems that are intelligent, programmable and integrated."
This is why aeSolutions links the capabilities of its cybersecurity division with the PHAs that it's long used to address process safety challenges. These security and safety functions are combined in its aeCyberPHA methodology, which applies ISA 99/IEC 62443 cyber risk assessment requirements that link realistic threat scenarios with known vulnerabilities and existing countermeasures, and couples them with credible consequences from the PHA to determine cyber risks. So far, aeCyberPHA has been applied in more than 70 industrial facilities.
Talk, inspect, detect
Another helpful but awkward method to address industrial cybersecurity begins with simple discussion to share common concerns and best practices, collaborate where possible, and develop unified responses by users, clients, contractors, system integrators and suppliers to cyber probes, intrusions and attacks.
The Industrial Internet Consortium reported April 9 that it's published its "IIC IoT Security Maturity Model (SMM): Description and Intended Use." Based on IIC's Industrial Internet Security Framework, SMM defines levels of security maturity for an organization to achieve based on its security goals, objectives and appetite for risk, which lets decision-makers invest only in security mechanisms meeting its needs. View it here.
Organization apply SMM by following a process. First, business stakeholders define security goals and objectives, which are tied to risks. Next, technical teams in the organization or third-party assessment vendors map these objectives into tangible security techniques and capabilities, and identify an appropriate security maturity level. Finally, the organization develops a security maturity target, which includes industry and system-specific considerations, and capture the current security maturity state of the system.
A second document, "The IIC Security Maturity Model: Practitioners Guide," will be released in the next several months and will contain technical guidance for assessment and enhancement of security maturity levels for appropriate practices.
Schaffer adds that implementing a successful cybersecurity program requires management buy-in and budget support from the start, as well as a thorough network audit and inventory including what it's communicating with and what protocols it's using.
"We love using tools like Wireshark packet analyzer software because it captures a baseline of what network traffic looks like, including speed, network latency and packets per second, and puts them in context," he explains. "A snapshot of a healthy network gives us a few things, such as if there's a problem, we can take a second capture, see if the latency has gone from 5 milliseconds (ms) to 130 ms or something like that, learn what's happening where, and get a better window for improved troubleshooting. This also helps us plan how and where to make a network more secure; determine which firewall rules to establish; decide which PLC can talk to which HMI; and create other rules we want."
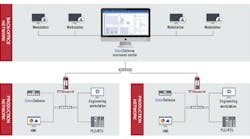
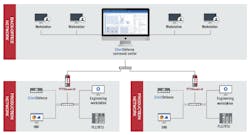
To further protect against threats and intrusions, Phoenix Contact recently invested in Netherlands-based Security Matters and its SilentDefense software, which identifies anomalous network traffic and lets users set up blocking rules in their firewalls. They report that SilentDefense, which employs DPI and its Industrial Threat Library of more than 800 ICS-specific threat indicators, is being integrated into Phoenix Contact FL mGuard routers and firewalls to produce networks that are more secure and resilient, and reduce unplanned downtime and mitigation costs (Figure 1).
Figure 1: Phoenix Contact recently invested in Netherland-based Security Matters and its SilentDefense software, which is being integrated into Phoenix Contact's FL mGuard routers and firewalls. SilentDefense lets users set blocking rules in their firewalls and enables them to identify anomalous network traffic. Source: Phoenix Contact and Security Matters
Anomalies and AI
Similarly, Edgard Capdevielle, CEO of Nozomi Networks Inc., reports his company's strategy is to connect with industrial networks without being intrusive, listen to their processes, build a baseline of the system's behavior and operating range, and inform clients when its goes outside it normal behavior.
"We have to assume that penetrations and hacks are already occurring, and we catch them, so they're not allowed to spend months inside of systems," he explains. "We interview the PLCs and processes at all phases of an operation by sitting on a network in read-only mode, and doing unsupervised learning about it. This enables us to create the baseline, detect slight deviations and gauge if they're potentially able to throw the process into a critical state."
Capdevielle adds that Nozomi's passive anomaly detection method isn't "process aware," but it's also different than primitive, rules-based, whitelisting methods and can be compared to advanced process control (APC), machine learning and artificial intelligence (AI) techniques. The firm's SCADAguardian appliance can be added physically as P500 appliances or virtually to a process application or equipment, routes read-only data to Nozomi, which parses existing protocols to reach operational information.
"We try to understand an individual process and map it, so we can base security on behavior because we know the phases and procedures of each application," he says. "If they're not interacting as expected, then we can report that something's been detected in ranked alerts according to degrees of criticality. If a super-critical anomaly is identified that needs fast action, we can integrate that action into the applicable firewall in real time and control that anomaly by blocking any serious command changes."
The European Commission's (EC) newly enacted General Data Protection Regulation (GDPR) took effect on May 25 and aims to protect the data and privacy of European Union (EU) citizens, plus give them better control over it—no matter where it's sent, processed or stored—even outside the EU, as is often the case on the Internet. The EC reports it developed the GDPR by beefing up its existing Data Protection Directive because 90% of Europeans were concerned about mobile apps collecting their data without their consent, while 70% were worried about companies using that information
Briefly, GDPR's rules include:
- The right of users to be "forgotten;"
- Easier access by users to their personal data;
- Right of users to know when their data has been hacked; and
- Data protection by design and default, which requires manufacturers to build security into their products and services, and make privacy-friendly default settings the norm for mobile apps and social networks.
Entities controlling data will be responsible and accountable for protecting it, using encryption and other techniques, and will be held liable if they don't do it. Sanctions will include warnings, audits and fines that could reportedly reach up to €10-20 million.
More information can be found here.
Enel had been using standard networking tools to handle its industrial control system (ICS), but many of its procedures were manual and time-consuming, plus data was hard to gather, correlate, understand and use. Enel also needed in-depth support of the IEC 60870-5-104 SCADA protocol, which is used for power system monitoring and control to comply with the security requirements of the IEC 62351 standard.
Consequently, Enel and Nozomi installed SCADAguardian at one regional control center as a pilot, tested and fine-tuned the deployment, and then rolled it out at all regional centers to monitor operations. They also deployed it at of the TSO interconnection centers to monitor links between Enel and Terna.
Finally, SCADAguardian's Central Management Console was installed to monitor, run and update the individual devices, and portable SCADAguardian P500 appliances were added to monitor and analyze segments requiring further examination and troubleshooting. As a result, Enel gained:
- Full visibility of its control network, including at remote sites;
- Enhanced operational insights, such as detecting misconfigurations, anomalous activities, critical states, and standard and advanced security attacks;
- Supervision using in-depth understanding of Enel’s ICS and supported SCADA application level protocols such as IEC 60870-5-104;
- Automatic, real-time notification of industrial events of interest, including alerts triggered by custom-designed rules and constraints; and
- Traffic analysis for current and future investigations.
"Through this partnership, we've made a substantial improvement in our remote control system," says Fredrico Bellio, head of power generation for Enel's remote control system. "Through an extensive production pilot, Nozomi proved its non-intrusive, in-depth technology improved the reliability, efficiency and cybersecurity of our remote controls. SCADAguardian is now a fundamental element of our network infrastructure and an essential tool for our daily activities.”
Dynamic cyber accessories
In conjunction with adopting risk-based methods such as cyberPHA, aeSolutions' Cusimano reports that a comprehensive industrial cybersecurity program also requires:
- A core team of those responsible for cybersecurity in a plant and all its systems;
- An experienced cybersecurity partner that can help with implementation, training and following the ISA 99/IEC 62443 standard and training;
- A common mission for the team to keep it focused long-term;
- An as-built model of the entire plant system;
- A phased approach, most likely with high-level cybersecurity assessments first;
- Using cross-training to develop a common cybersecurity language;
- Documenting deliverables, such as ICS security architecture drawings, cybersecurity specifications, vulnerability assessments, zone and conduit models, deployment strategy, cybersecurity policies and procedures; and
- Employing sustainable processes and systems that can be maintained and upgraded over the years.
"The cyberPHA process is pretty intensive, but it really works and produces fantastic results, and it gives users a basis for their system design," explains Cusimano. "Air Products implemented this process on a number of its plants, and it has also given them a good foundation for defending why they're spending on cybersecurity."
Cusimano adds that with good risk information, users can:
- Determine what plants and processes need to be addressed first;
- Intelligently design and apply countermeasures to reduce and manage risk, such as network segmentation, access control, network hardening and intrusion detection;
- Prioritize resources and activities;
- Evaluate countermeasures based on their effectiveness compared to their cost and complexity; and
- Establish a firm basis for present and future cybersecurity decisions.
"Air Products determines its target architecture for cybersecurity based on analysis, and revisits it every couple of years make sure these systems and the architecture are still valid given the changing conditions that are out there," explains Cusimano. "The cybersecurity world is not one that stays the same. It's always dynamic, and you have to keep your cyber defenses updated."