Network security and engineering are still not on the same page, not even the same book
My research and observations indicate the current approach to cybersecurity in critical infrastructures typically has the CISO lead IT and OT cybersecurity organizations. This is an unbalanced view that has led to a culture gap between the network security organizations the CISO leads and the engineering/operation’s organizations where OT resides. This approach is prevalent throughout the cybersecurity community as can be seen by the October 2024 McCray Institute’s report, “Securing America’s Digital Future: A Bipartisan Cybersecurity Roadmap for the Next Administration, Recommendations from a Task Force of leading Cybersecurity Experts”. ISA TR84.00.09, “Cybersecurity Related to the Safety Lifecycle,” offers a different and promising approach to improve control system cybersecurity and process safety while at least partially addressing the culture gap.
CISOs need to understand the full depth and breadth of cybersecurity. OT cybersecurity issues are far more serious than, for example, the billing system compromises in the recent American Water incident and elsewhere. The cybersecurity of OT systems is important because of the possibility of both physical damage and disrupted/off-specification product delivery. OT systems utilize instrumented control and protection systems that, if unintentional or maliciously compromised, can involve significant consequences, e.g., refinery explosions and pipeline ruptures with potential fatalities, water issues making people sick, medical devices injuring people, airplane and train crashes with potential fatalities, etc. These physical types of control system issues are generally not identified as cyber-related; however, can have more business impact and certainly have equal cyber vulnerabilities.
Get your subscription to Control's tri-weekly newsletter.
There’s a general lack of integration of engineers and plant floor operation’s personnel and their expertise with IT and OT cybersecurity professionals. This is most likely due to a lack of understanding of how their roles overlap.
In the blog, “OT/control system cybersecurity has changed and not for the better”, I sought to demonstrate how in 2001 control system cybersecurity was an engineering issue to be addressed with IT support. Now, however, critical infrastructure cybersecurity appears to be considered a network security issue, often approached with little or no engineering participation. In the blog, I mentioned that one electric utility is at present addressing control system cybersecurity, and I don't know of any water utility doing this.
That blog elicited the following feedback from the CISO of one of the largest water utilities in the U.S.
CISO feedback: “I think Cyber Defense is a complex subject and one that, frankly, cannot be over simplified or distilled into engineer versus security professional. Perhaps it would be good to have an open conversation with people on the front lines of cyber defense about what they look at and for. My experience with cyber defenders is they spend a great deal of time understanding the adversary and the avenues of approach to their targets. This includes insider threats and threats from inadvertent harm. I simply don’t agree with the blanket assertion that cybersecurity professionals are not addressing OT security or that water utilities are not tackling the issue.”
My response: Unfortunately, engineers are generally not on the front lines of cyber defense. Understanding the adversary is important, but it is also important to understand the process you are trying to protect, in this case, the water treatment or delivery process.
CISO feedback: “I think the issue is simpler than this. I agree with the points made about ICS security, more specifically I don’t disagree with you. I believe we are at risk of talking past each other if we can’t see that cyber defense, is a more holistic thing. For example, from a threat actor perspective, if the systems needing protection have the proper physical security measures and the cybersecurity access controls are applied appropriately to things like the jump host used to gain access to a management interface, then the protected system’s risk of compromise due to a malicious actor are substantially reduced. If you are guarding the throne in a castle, one has to be able to breach the castle. There could be moats with crocodiles and towers with archers with visibility on all roads leading to the castle, and locked doors inside the castle separating the various area and levels. Yes, there are things in ICS that are vulnerable, but I stand by the sentiment that it is not engineers or even cyber educated engineers alone that can protect these systems but engineers working with cyber professionals that will make the difference.”
My response: I agree with the need to have cyber professionals and engineers work together, but the engineers are not, in fact, generally involved. In fact, many control system field devices today do not have the technical capability to employ cybersecurity technologies including access control and authentication. As a result, compensating controls must be employed that require engineering expertise.
CISO feedback: “Cybersecurity is more than forensics or a collection of tools. It’s a discipline. It is a professional methodical approach to protecting critical assets and data. It is in short, the digital version of protecting a castle. I think it is helpful to compare cyber defense efforts to operations on a battlefield more than to look at individual components or exposures absent of context. In short, you can’t steal the Crown Jewels if you can’t get into the castle or escape it once inside. This is accomplished through technical and procedural efforts. It starts at the manufacture, it is built into the systems, assembled in operation, it is the requirements for access, employee background checks, Identity and Access Management, Network Access Control, and yes, some good old fashioned IT know-how as well as document understanding of the process being protected. I am confident that we as a community working with our partners in AWWA, CISA, the FBI and our other Federal and State partners along with our vendor partnerships, will get better together.”
My response: Engineering is also a discipline that requires a professional methodical approach to maintaining system reliability and safety. Unfortunately, as there is no cybersecurity in the control system field devices, they require compensating controls that come from years of engineering know-how for the process being protected, in this case the treatment and delivery of water. AWWA, CISA, FBI, and other partners need to work with engineering organizations to identify and address cybersecurity threats to water systems.
The gap in understanding of control systems by water CISOs is not limited to that one utility or sector. Several years ago, in reviewing the cybersecurity program of another large water utility, the issue of process sensor cybersecurity was raised. The SCADA operator who was part of the utility’s cybersecurity team stated that process sensors and actuators were outside the scope of their cybersecurity program. Recently, the water utility CISO was asked how many field control system devices the water utility had installed. The response only included HMIs, which are not field devices. In addition, PLCs, basic process control systems, process sensors, actuators, drives, and analyzers were not included in the CISO’s response.
In both cases, the CISOs did not have previous OT/control system experience. As can be seen in these examples, the CISOs gaps in knowledge about control systems and operational issues are why I wrote the paper “Who’s in charge of OT security."
Engineers also need to understand and be an active part of cybersecurity (risk management).
In the September 2024 issue of Control magazine, John Rezabek contributed an article, “A complex DCS quandary.” He writes: “In the early days of this technology, all engineers who wanted such features were engaged and present for factory acceptance tests, commissioning, and startups. They knew about the clever tweaks in the blockware and might be on hand if one setting or another caused some befuddling behavior. Whoever is left after those veterans move on or retire is often stuck with befuddling behavior with no clear remedy. DCS support roles fall to non-process disciplines like network specialists and active domain administrators. These are valuable skills and roles, but how many know the purpose or even existence of a setting such as ‘use uncertain as good?’ In our digital world, we should employ all the power at our command to ensure safety, stability, and reliability of controls. However, everyone clicking a mouse should be trained in all of the options, including all the gotcha moments that will someday arise.”
Cybersecurity was not specifically mentioned in Rezabek’s article, although it should be explicitly acknowledged. Everyone clicking a mouse should also include personnel whose primary focus is cybersecurity, not just the control engineering and operator functions, etc.
The Competence Annex in IEC 61511, "Functional safety - Safety instrumented systems (SIS) for the process industry sector", is intended to provide guidance of a competence management system. Many SIS related events and incident investigations identify human error as a cause or contributing factor. The intention of a competence management system is to ensure competence requirements are met before an individual is assigned or continue to work on a SIS lifecycle related activity. There are competency requirements in clause 5.2.2 of ANSI IEC-61511-1.2016. However, cybersecurity is not mentioned. October 28, 2024, I provided this annex to ISA84 to have cybersecurity competence integrated with process safety competence.
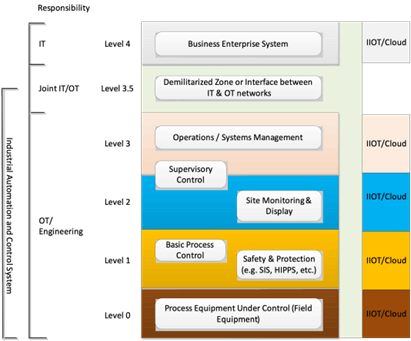
ISA TR84.00.09, “Cybersecurity Related to the Safety Lifecycle,” is the technical report developed by the International Society of Automation (ISA) that addresses the intersection of process safety and cybersecurity. The technical report part 1 was published in 2024. A use case is currently being developed as part 2. Unfortunately, there has been NO participation from the electric or water industry even though power and water facilities have the same or similar equipment and security needs as process facilities. Consequently, it is recommended that the ISA TR84.00.09 be used where appropriate for electric and water facilities to safely secure their OT and control system assets. An excerpt from the TR shows the interface and overlap between IT and OT engineering.
ISA TR84.00.09 specifically addresses the need for control and safety engineers to work with OT security engineers and physical security as there is limited understanding of how a security breach can lead to significant consequences or failure in a cyber-physical system or OT system. The impacts of a cyber-physical incident extend beyond traditional IT concerns as they include physical safety, environmental damage, harm to people, and economic consequences. OT may delegate some security tasks to IT who will act as a service provider to OT. As such, there is no mention of the CISO role in ISA TR84.00.09, although the need for IT security input is included.
Conclusion
There is a culture gap (amounting to a chasm, actually) between cybersecurity managed by the CISO on the one hand and engineering and operations personnel responsible for OT on the other. Part of the gap comes from many CISOs’ (and their teams) lack of experience and understanding of control / protection systems and devices making up such systems as well as the lack of understanding of engineering and operations requirements and work processes. Engineering and Operations have a corresponding understanding gap regarding cybersecurity. The culture gap between cybersecurity and engineering/operations results in both sides either not talking or talking past each other. This is why I wrote the paper, “Who’s in charge of OT Security.” Cyber attackers recognize these gaps and are exploiting them. However, utilizing the approach in ISA TR84.00.09 can help protect the control and safety systems used in critical infrastructures, including the electric and water sectors, and hopefully close these culture gaps. Industry and government organizations should recognize and address this critical culture gap.