Improving reliability and safety with instrument asset management systems
Modern petrochemical facilities can have thousands, or even tens of thousands, of instruments. Each "smart" instrument may provide a dozen or more data points in addition to the measured variables. Add in configuration, calibration and maintenance data, and that's a lot of information to keep track of over the long term, giving personal meaning to Clark's Law: "Data will fill up available space."
Along with the signals we normally use, we can extract a lot of information from this cornucopia of data by using data analytics. Unfortunately, there are no analysis standards directed specifically at instrument asset management systems (IAMS), but there is a series of international standards under ISO 55000 that provide a benchmark for asset management systems in general.
The rise of ISO 55000
Plants can generally achieve significant reductions in operating costs and downtime as a result of implementing an effective asset management strategy (with the key word being "effective"). In 2002-2004, the British Standards Institute introduced PAS 55, which was the first publicly available standard for management of physical assets. PAS 55 was widely adopted in utilities, transport, mining, process and manufacturing industries worldwide.
William Mostia, PE, is a fellow at SIS-TECH Solutions and is a frequent Control contributor.
In 2008, the PAS 55 standard underwent a substantial revision by 50 organizations from 15 industry sectors in 10 countries, and served as the basis for developing the new ISO 55000 series of international standards in 2014. ISO 55001 defines requirements for an asset management system in much the same way as ISO 9001 specifies the requirements for a quality management system.
ISO 55000 offers a more comprehensive asset management focus, not focused solely on physical assets, but also other types of assets including non-physical assets, tangible and intangible, such as software, experience, reputation, brand, intellectual property, etc. It has a category, Critical Asset, which would include safety-critical instrumentation.
Control systems are smart assets
Control and safety systems contain many different types of "assets." Some of these are the traditional physical assets, such as sensors, valves, and controller components, that would appear on the accountant's ledger in black and white. Less obvious, but also important, are tangible and intangible assets, such as the software and its configuration, that help the hardware to control the process to make product and keep safe your people, process expertise, engineering expertise and process knowledge. The skills, capability, knowledge, specific process experience of your company's personnel, and their ability to implement the power of your controls often are considered the assets that make the difference between success and failure, and it makes sense to manage these as well.
With the introduction of microprocessor-based smart instruments in 1983 and development in the 1990s of digital communication protocols such as HART, Foundation fieldbus, Profibus, and their brethren, IAMS have become increasingly commonplace. They are touted to cut operating and maintenance costs and reduce downtime while improving asset efficiency, uptime and reliability. They also are said to improve effectiveness of maintenance and operations staff, and improve the safety of some maintenance activities, to mention a few of the claims by IAMS suppliers. Experience has also shown that an IAMS can be of significant benefit during commissioning of smart instrumentation. Another area of benefits that is not always mentioned is process safety, and the aspects of reliability that impact process safety.
Asset management's role in process safety
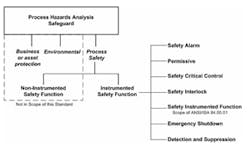
Layers of Protection Analysis (LOPA) identifies independent layers of protection (IPLs) that are needed to reduce the identified risk to the corporate risk criteria. Many of these are instrumented IPLs, which are classified as safety controls, alarms, and interlocks (SCAI) in ANSI/ISA-84.91.01-2012 - "Identification and Mechanical Integrity of Safety Controls, Alarms, and Interlocks in the Process Industry" (see figure 1). The Safety Instrumented Systems (SIS) standards ANSI/ISA 84.00.01/IEC 61511 have requirements to manage functional safety associated with SIS and require that the performance of the SIS be verified over the SIS lifecycle.
To help evaluate the performance of SIS over its lifecycle not only requires collecting failure rate and demand rate data, but also sustaining the effort over the SIS lifecycle, which can be 10-15 years or more. An IAMS can provide a structure for this effort, and since is doubtful that a paper system would be very successful in sustaining this effort over changes of administration of the system, an asset management system configured to manage safety critical instrumentation is a must.
Instrument reliability affects process safety
Process safety can be strongly affected by the reliability of its control and safety systems. Obviously, SIS contribute to the safety of a facility and have a strong formal system of standards and body of practice in industry. The area of the non-SIS instrumented safety systems is a bit murkier in regards to requirements. There certainly is agreement on what the properties of an IPL should be (e.g. independence, specificity, dependability, auditability, security, and management of change). In the United States, these instrumented safety systems would come under OSHA PSM 1910.119 and have requirements similar the SIS standards but with much less detail and guidance on how to implement the requirements and achieve what OSHA calls "recognized and generally accepted good engineering practice (RAGAGEP)." Note that OSHA recently issued a Memorandum for Regional Administrators and State Plan Designees on June 5th, 2015, that provides additional general guidance on enforcement of the Process Safety Management (PSM) Standard's RAGAGEP requirements.
A review of any LOPA will show that a basic process control system (BPCS) failure is a common initiating cause. While we will not probably improve the BPCS failure frequency used in the LOPA, if we can improve the reliability of our control system, we can improve the safety of the facility.
There may also be an overlap between some of the components used in the BPCS and the SIS, particularly on the input side. For example, it is not uncommon for facility to use the same model transmitter as the safety transmitter, or the same model without the SIL approval papers. So reliability improvements can benefit both sides.
There is also a push in industry to collect failure rate and failure mode data to better evaluate current technology in reliability calculations and to improve instrument reliability. In 2012, an industry consortium formed the Instrument Reliability Network (IRN) (https://irn.tamu.edu/), which is hosted by the Mary Kay O'Conner Process Safety Center at Texas A&M University. The IRN has the goal of developing common tools and methods for collecting quality instrument reliability data, which would benefit industry. An IAMS combined with a properly configured maintenance management system could collect this kind of information, which could not only benefit your company by improving your instrument reliability, but by sharing sanitized data with the IRN, could help develop industry benchmarks for SIS and control system performance.
Then there's security
Security is also an issue for management of safety critical/SCAI assets in an IAMS. If the SCAI management is a separate system, the separation can provide an element of security if the access population is limited. When the SCAI management portion is an add-on to a general-purpose instrument asset management system or general-purpose AMS, the population with access may include everyone up to the whole instrument maintenance department due to its usefulness. Default or shared passwords should not be used to access safety critical/SCAI instrumentation.
The access to safety critical instrumentation/SCAI should be tightly controlled to only those personnel who are authorized to perform SIS/IPL maintenance and modification activities to help prevent inadvertent or unauthorized changes in safety critical instrumentation. Procedures should be established to ensure proper usage of the handheld communicators when working with critical instrumentation.
Cybersecurity must also be a consideration to help limit any internal or external attempts to access and change data that could affect the safety of a facility. Adequate firewall and zonal segregation should be provided. Something as simple as plugging in a thumb drive where the user is unaware that a virus like the Stuxnet cyber worm was riding on board or worse, an intentional act of sabotage, can compromise your whole system and the safety of your facility in mysterious and unknown ways. Wireless also offers new possibilities of connectivity to IAMS but opens the door to potential cyber vulnerabilities. Cyber security protection is longer an option for most petrochemical operations today.
The IAMS can also help collect leading and lagging process safety metrics (a la API 754) for management. It can also facilitate collection of control system performance data on a per-loop basis. Some common control loop statistics are that 30% of our control loops are on manual while another 10-20% not performing well. If this is the case, an ISAM system capable spotting these problem loops could be invaluable.
Make an audit trail
One of the other key powers of the IAMS is providing an audit trail for changes including MOC, configuration and calibration data, version management, etc. This can be critically important for managing SCAI and surviving a company or third-party audit, or a visit from OSHA.
Maintaining an audit trail for meeting the SIS standards and regulatory purposes can be difficult. One of the powers of the IAMS is that it can typically provide an audit trail for changes and testing, inspection and calibration. IAMS can be used to as an essential part of SIS periodic inspection and proof test processes. Procedures can be created within the AMS software to help ensure consistency and documentation as required by IEC 61511, and potentially, to help create testing metrics for management.
IAMS that have SIS management capability typically have the ability to schedule when proof tests and inspections must be performed; to work with the maintenance management system to arrange for notifications and work orders for testing; and to later tabulate testing result and metrics. If the IAMS allows multimedia formats, enhanced procedures can be incorporated for maintenance, testing and inspections.
Why do without?
An instrument asset management system is something that you can hardly do without to meet the myriad requirements of a modern petrochemical plant, which aren't going to get any simpler and will probably get more complex. Most manufacturers of modern DCSs and some PLCs (e.g. ABB, Emerson, Honeywell, Invensys, Rockwell, to mention a few) provide some form of asset management these days, and some also provide SIS asset management. The SCAI world discussed above may be new to some, as is IPL asset management. If your DCS/PLC system offers these management systems (and they are not generally free), they should be evaluated to see if they will be a good fit for your overall control and safety systems, and your instrument management goals.
If they don't, look at third-party IAMS. Make sure the IAMS is vendor-agnostic, as a facility may have instruments from many different manufacturers and managing only a subset is unlikely to give your desired rate of return and meet your goals. IAMS interconnectivity is also important to allow connectivity to other plant systems and to enterprise systems (through suitable firewalls).
Be wary of snake oil salesmen and understand that the benefits of IAMS are strongly affected by implementation commitment, the utilization rate of its capabilities, and the effectiveness of available support. Competent internal and external support people must be available to ensure the system is sustainable over the long term. Bespoke systems are to be avoided, but the system should have the flexibility to grow and adapt to future needs. A management champion and an implementation champion are, by the nature of the beast, a necessity for a successful, sustainable system.
You also cannot make it too hard on the instrument technician, as he is an important part of a successful system. I remember being told as a young instrument engineer, back when the dinosaurs roamed the earth or close to that time, that if I bought or designed something that made the maintenance technician's life harder or if they collectively did not like it, my project would likely fail for reasons other than technical. Thirty five years later, nothing in my experience has disabused me of that idea. I always got Maintenance on my side by convincing them ahead of time. You might be surprised how far a little courtesy and asking for input goes, and you might find that the technicians come up with some excellent ideas and can facilitate as opposed to impede the implementation and sustainability of the IAMS. This support is almost a necessity for this type of project.
Figure 1: The ability of an instrumented safety function to fulfill its role as a layer of protection in a process hazards analysis depends on managing the asset integrity of safety equipment from alarms and controls to interlocks and emergency shutdown systems. Source: ANSI/ISA-84.91.01 – 2012.
Latest from Asset Management

Leaders relevant to this article: