Developing Control System Security Standards
"The nicest thing about standards is that there are so many of them to choose from."
- Ken Olsen, founder of Digital Equipment Corp., 1977
"Laws are like sausages. It is better not to see them being made."
- Otto von Bismarck
I offer a somewhat different perspective, based on my experience with the ISA99 committee on Industrial Automation and Control Systems Security.
Committee Overview
The ISA99 committee currently has over 500 members, organized into several work and task groups. Each of these groups is focused on a particular area, with specific objectives and assigned work products.
While the majority of the registered committee members could be characterized as "lurkers" who have presumably joined in order to monitor developments in this area, there is a core group of dedicated volunteers, who have given generously of their time to identify and develop several concepts that are slowly, but surely making their way into common practice.
Committee Work Products
Since its inception in 2002, this committee has produced several standards and technical reports, with several others in various stages of development. The name of this series was originally ISA-99, as in "the ISA-99 standards," but more recently they are being rebranded using the nomenclature "ISA-62443" as a means of emphasizing the alignment with the corresponding work products from IEC with the assigned number "IEC 62443."
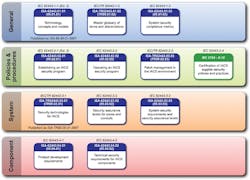
An overview of the committee work plan is shown in Figure 1.
Figure 1. An overview of the committee work plan.
This plan calls for the development of at least 11 separate work products (i.e., standards or technical reports) that collectively address the subject of IACS security. While the majority of these will be produced by the ISA99 committee, there is also provision for inclusion of work products sponsored by IEC Technical Committee 65, Working Group 10.
These work products are in turn organized into four tiers.
Documents in the first tier (ISA-62443.01.xx) address general subjects that establish the basis of the series. They include the first standard in the series, originally completed in 2007, as well as a master glossary and a description of common metrics. The other two are currently in development and may in fact not be released until all other documents are completed.
Documents in the second tier (ISA-62443.02.xx) address various aspects of how to define and operate an effective security program for industrial control systems. Although program definition and operation are currently addressed in separate work products, the direction is to consolidate these into a single standard.
[pullquote]Finally, the documents in tiers three and four delve into the requirements that must be met at both the overall systems and the component level in order for a control system to be considered secure. Of these, the ISA-62443.03.03 standard has recently been approved by the committee and is being revised for publication. The corresponding IEC 62443 version has also been approved.
A detailed description of each of the work products is beyond the scope of this article, but more information is available on the committee web site, including copies of the current working drafts of each document.
Fundamental Concepts
There are several fundamental concepts that collectively form the basis for the ISA-62443 series.
The first of these is a set of Foundational Requirements that in turn is the starting point for more detailed requirements in the remaining documents in the series. They include:
- Identification and authentication control
- Use control
- Data integrity
- Data confidentiality
- Restricted data flow
- Timely response to events
- Resource availability.
Each of these is described in more detail in ISA-62443.01.01.
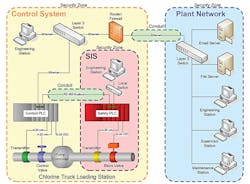
The concept that perhaps has gained broadest acceptance is the practice of network segmentation, described in the standards as the definition of zones and conduits. Briefly this concept involves the logical division of a complex control system into a series of zones, each with a specific set of security related characteristics. These zones are interconnected via logical pathways called conduits. This approach follows the well-established principle of dividing a large problem into smaller pieces in order to address the stated requirements. Introduced in ISA-62443.01.01, the application of this concept is explored in much more detail in a companion standard (ISA-62443.03.02) that is devoted to the subject. Each of these standards is currently under revision or development. The zones and conduits concept is illustrated in the example shown in Figure 2.
Figure 2. Each zone with similar security requirements is connected via a logical pathway called a conduit.
The third fundamental concept is that of security levels. This concept is being developed and refined by the committee and will be described in detail in ISA-62443.01.01 and ISA-62443.03.02. Security levels are similar and complementary to the safety integrity level (SIL) concept that is described in standards such as ANSI/ISA-84.00.01-1996. Four separate types of security levels have been identified, corresponding to the desired or target level, the planned level for a particular system, the achieved level and the level of capability.
Security levels become an important attribute in an IACS zone once the zone boundaries and conduits have been defined. The levels are assessed over the lifecycle of the design.
This security level lifecycle is the fourth fundamental concept of the ISA-62443 series. A zone is assigned a target security level during the Assess phase of the security lifecycle. Countermeasures are implemented during the Implement phase to meet the target security level for the zone.
The achieved security level for a zone depends on various factors. In order to ensure that the achieved level is better or equal than the target level for the zone at all times, the countermeasures are audited, tested and upgraded, if necessary, during the Maintain Phase of the security lifecycle.
A much more detailed description of security levels and their determination will appear in the next edition of ISA-62443.01.01.
These Fundamental Concepts are an important element of the entire ISA-62443 series of standards. These and many other topics are more fully developed in other standards in the series.
The work of the committee takes place in meetings of the various work and task groups, the vast majority of which are conducted in the form of teleconferences. This allows for maximum flexibility and minimum cost for participation. Face-to-face meetings are conducted as required to address major issues and review and revise committee plans.
Conclusion
Let's go back to the perspectives offered at the beginning of this article. Are there several standards in the area of control systems security? Definitely, but at least in the context of the ISA99 effort, this complicated topic has been broken into smaller parts, each to be addressed by one or more standards in a series. Moreover, additional related topics are included through liaison relationships with organizations such as IEC.
Are the processes for standards development complicated? Perhaps, but they have been well-defined and are being applied in a manner that encourages, if not requires, broad and open participation in order to achieve the desire results. Furthermore, the individual members do not have to understand that myriad of procedural details in order to make a meaningful contribution.
Finally, does the process take too long? Possibly, but the true value of the concepts developed in this process can be harvested long before the final standards are completed or published. Participation in or even just monitoring the work of the committee is an excellent way to track developments and apply these concepts now.
More detailed information about the structure, operation and work products of the ISA99 committee can found at the Wiki site http://isa99.isa.org/.
About the Author
Eric C. Cosman
Eric C. Cosman

Leaders relevant to this article: